EDPB Seeks Views On Right To Access Under GDPR
Dutch DPA fines Apple; UK's CMA fines Meta/Facebook; Belgian DPA finds that advertising transparency and consent framework runs afoul of GDPR
First, the Wavelength has transitioned to a paid product, but there will still be a free version available. The transition to a subscription model starts today.
The European Data Protection Board (EDPB) is asking for feedback on its draft “Guidelines 01/2022 on data subject rights - Right of access” under the General Data Protection Regulation (GDPR) as part of its larger, ongoing mission to ensure the European Economic Area’s (EEA) data protection authorities (DPAs) interpret and apply the data protection regime uniformly, advise EEA residents of their rights, and inform controllers, processors, and other stakeholders about their obligations and responsibilities. The EDPB’s guidance and interpretations have weight throughout the world in a number of different ways. First, entities headquartered outside the EEA may be subject to the GDPR. Second, DPAs around the world have often worked with or even against the GDPR, making the EDPB’s views informative of other data protection schemes throughout the world. Third, the Board stresses that its interpretation is grounded in caselaw from the Court of Justice of the European Union (CJEU), the highest court in the bloc.
In this instance, the EDPB is construing more than just the GDPR, for “[t]he right of access of data subjects is enshrined in Arti. 8 of the EU Charter of Fundamental Rights.” The EDPB added that “[i]t has been a part of the European data protection legal framework since its beginning and is now further developed by more specified and precise rules in Art. 15 GDPR.” Moreover, the Board “considers it necessary to provide more precise guidance on how the right of access has to be implemented in different situations.”
As a reference point, here is Article 15: Right of access by the data subject:
The EDPB summarized this foundational right that has a few discrete components:
Under the GDPR, the right of access consists of three components i.e. confirmation of whether or not personal data are processed, access to it, and information about the processing itself. The data subject can also obtain a copy of the processed personal data, whereas this possibility is not an additional data subject right but the modality of providing access to the data. Thus, the right of access can be understood both as the possibility of the data subject to ask the controller if personal data about him or her are processed and as the possibility to access and to verify these data. The controller shall provide to the data subject, on the basis of his/her request, the information falling within the scope of Art. 15(1) and (2) GDPR.
In more depth, the Board construed this fundamental, foundational right:
The right of access is thus designed to enable natural persons to have control over personal data relating to them in that it allows them, “to be aware of, and verify, the lawfulness of the processing” More specifically, the purpose of the right of access is to make it possible for the data subject to understand how their personal data is being processed as well as the consequences of such processing, and to verify the accuracy of the data processed without having to justify their intention. In other words, the purpose of the right of access is to provide the individual with sufficient, transparent and easily accessible information about data processing, regardless of the technologies used, and to enable them to verify different aspects of a particular processing activity under the GDPR (e.g. lawfulness, accuracy).
So, to sum up, in the EEA, the right of access is in place so that people can exercise their rights in a meaningful way, for any person is able to determine which information a controller holds and processes. Inherent in the right of access is a right often split off and labeled a right to correct in many bills in the United States (U.S.) Nonetheless, under the GDPR, the right of access also entails the right to access the personal data a controller has and being able to verify its accuracy and correct it if needed.
The EDPB continues by observing that other GDPR rights are rooted in the right of access even though they may be exercised or vindicated without resort to this right:
In accordance with CJEU decisions5, the right of access serves the purpose of guaranteeing the protection of the data subjects’ right to privacy and data protection with regard to the processing of data relating to them and may facilitate the exercise of their rights flowing from, for example, Art. 16 to 19, 21 to 22 and 82 GDPR. However, the exercise of the right of access is an individual’s right and not conditional upon the exercise of those other rights and the exercise of the other rights does not depend on the exercise of the right of access.
And those rights the EDPB said the right to access guarantees are:
§ Article 16: Right to rectification
§ Article 17: Right to erasure (‘right to be forgotten’)
§ Article 18: Right to restriction of processing
§ Article 19: Notification obligation regarding rectification or erasure of personal data or restriction of processing
§ Article 21: Right to object
§ Article 22: Automated individual decision-making, including profiling
§ Article 82: Right to compensation and liability
Unlike a number of laws and proposed data protection laws in the U.S., in the view of the GDPR, the right of access is not subject to the discretion of a controller unless the request is excessive:
Given the broad aim of the right of access, the aim of the right of access is not suitable to be analysed as a precondition for the exercise of the right of access by the controller as part of its assessment of access requests. Thus, controllers should not assess “why” the data subject is requesting access, but only “what” the data subject is requesting (see section 3 on the analysis of the request) and whether they hold personal data relating to that individual (see section 4). Therefore, for example, the controller should not deny access on the grounds or the suspicion that the requested data could be used by the data subject to defend themselves in court in the event of a dismissal or a commercial dispute with the controller.
The EDPB articulated its general principles of the right of access:
When data subjects make a request for access to their data, in principle, the information referred to in Art. 15 GDPR must always be provided in full. Accordingly, where the controller processes data relating to the data subject, the controller shall provide all the information referred to in Art. 15 (1) and, where applicable, the information referred to in Art. 15(2). The information must be complete, correct and up-to-date, corresponding as close as possible to the state of data processing at the time
The EDPB summarizes the matters it discusses in much greater detail in how controllers should respond to requests to exercise the right of access:
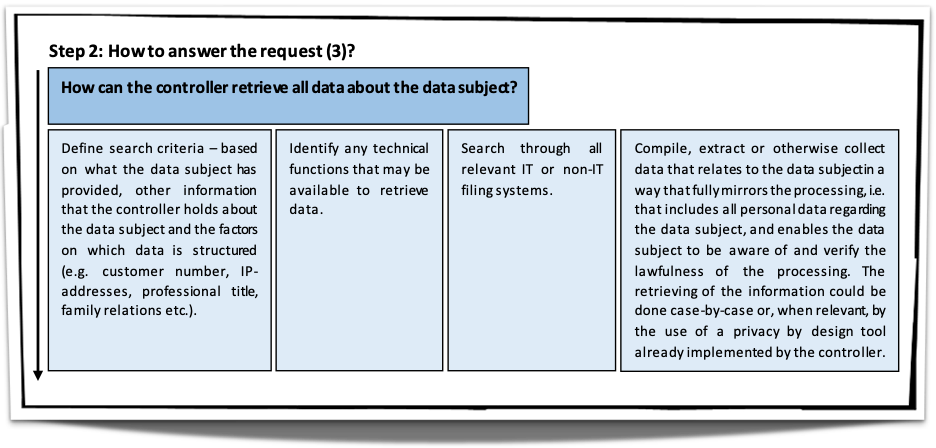
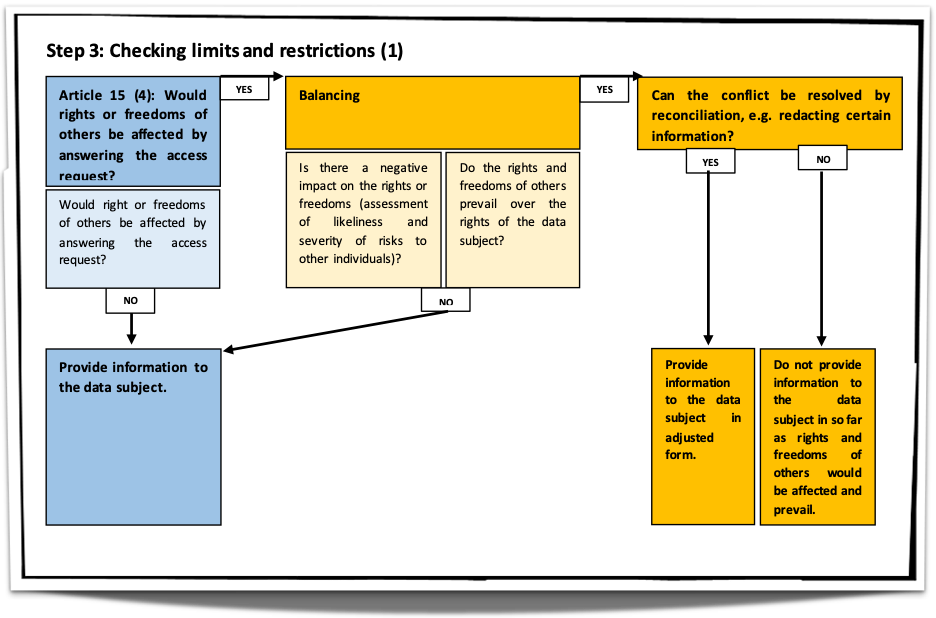
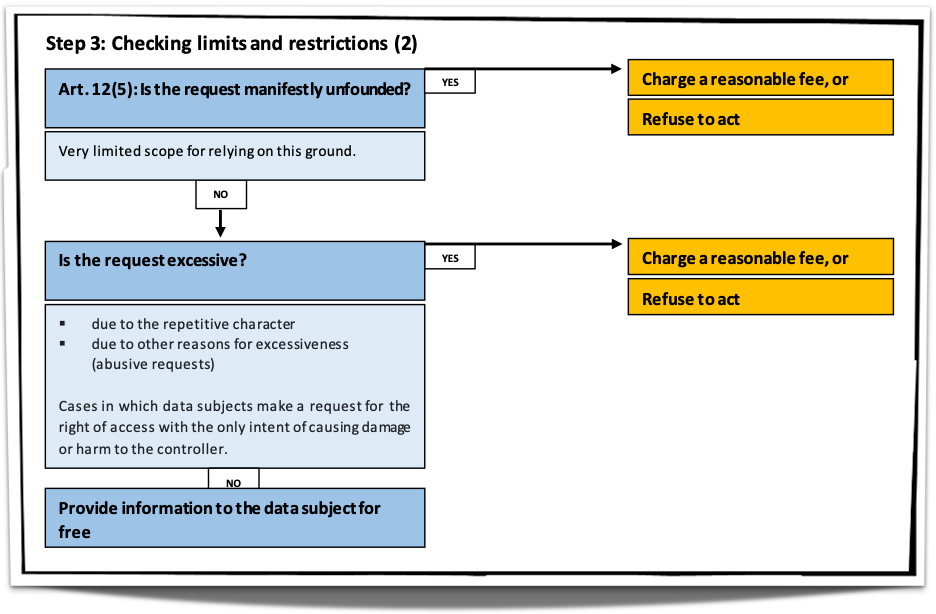
When receiving requests for access to personal data, the controller must assess each request individually. The controller shall take into consideration, inter alia, the following issues, further developed in the following paragraphs: whether the request concerns personal data linked to the requesting person and who the requesting person is. This section aims to clarify what elements of the request for access the controller should take into account when carrying out its assessment and to discuss possible scenarios for such an assessment as well as its consequences. The controller, when assessing a request for access to personal data, shall also take into account, pursuant to Art . 12(2), the obligation to facilitate the exercise of the data subject rights, while keeping in mind the appropriate security of the personal data.
Discussing and analyzing the detail of the guidelines is outside the scope of this post. However, the Board made available the following flowcharts to summarize how controllers should assess requests.
Other Developments
Photo by Mikhail Nilov from Pexels
§ Belgium’s L'Autorité de protection des données (APD) “has found that the Transparency and Consent Framework (TCF), developed by IAB Europe, fails to comply with a number of provisions of the GDPR” according to the agency’s statement. The APD stated:
o The TCF is a widespread mechanism that facilitates the management of users’ preferences for online personalised advertising, and that plays a pivotal role in the so called Real Time Bidding (RTB). The BE DPA imposed a €250.000 fine to the company, and gives IAB Europe two months to present an action plan to bring its activities into compliance.
o Contrary to IAB Europe’s claims, the Litigation Chamber of the BE DPA found that IAB Europe is acting as a data controller with respect to the registration of individual users’ consent signal, objections and preferences by means of a unique Transparency and Consent (TC) String, which is linked to an identifiable user. This means that IAB Europe can be held responsible for possible violations of the GDPR.
o The BE DPA identified a series of GDPR infringements by IAB Europe :
§ Lawfulness : IAB Europe failed to establish a legal basis for the processing of the TC String, and the legal grounds offered by the TCF for the subsequent processing by adtech vendors are inadequate;
§ Transparency and information of the users : the information provided to users through the CMP interface is too generic and vague to allow users to understand the nature and scope of the processing, especially given the complexity of the TCF. Therefore it is difficult for users to maintain control over their personal data;
§ Accountability, security and data protection by design/by default : In the absence of organisational and technical measures in accordance with the principle of data protection by design and by default, including to ensure the effective exercise of data subject rights as well as to monitor the validity and integrity of the users’ choices, the conformity of the TCF with the GDPR is not adequately warranted nor demonstrated;
§ Other obligations pertaining to a controller processing personal data on a large-scale: IAB Europe has failed to keep a register of processing activities, to appoint a DPO and to conduct a “DPIA” (data protection impact assessment).
o In view of these infringements, the Litigation Chamber of the BE DPA has decided to impose serious sanctions, particularly because the TCF may lead to a loss of control of their personal information by large groups of citizens. The Litigation Chamber therefore imposed an administrative fine of 250.000 EUR on IAB Europe. What’s more, it ordered the company to undertake a series of corrective measures aimed at bringing the current version of the TCF into compliance with the GDPR.
o These measures include (among others) :
§ the establishment of a valid legal basis for the processing and dissemination of users' preferences within the context of the TCF, as well as the prohibition of the use of legitimate interest as a basis for the processing of personal data by organisations participating in the TCF;
§ the strict vetting of participating organisations in order to ensure that they meet the requirements of the GDPR.
o The BE DPA gives IAB Europe two months to present an action plan to implement these corrective measures.
o This decision can be appealed.
§ The United Kingdom’s (UK) Competition and Markets Authority (CMA) fined Meta/Facebook “£1.5m after it failed to alert the CMA in advance of key staff leaving the company, which is required by the CMA’s initial enforcement order” per its statement. The CMA stated:
o It is standard practice for the CMA to issue an initial enforcement order (IEO) at the start of an investigation into a completed merger. This makes sure the companies involved continue to compete with one another as they would have before the deal took place. It also prevents the companies from integrating further while a merger review is underway. The CMA imposed this type of order on Meta, formerly known as Facebook, in June 2020 in relation to its purchase of Giphy.
o This order required Meta to actively inform the competition authority of any ‘material changes’ to the business, including resignations of key staff, and then seek prior consent before rehiring or redistributing responsibilities. Meta failed on both accounts following the resignation of 3 key employees and the reallocation of their roles. These 3 individuals had previously been included on a list of key staff provided to the CMA by Meta, reflecting their importance.
o This is not the first time Meta failed to inform the CMA of staff changes at the appropriate time, having failed to do so multiple times in 2021.
o When issuing fines, the CMA takes into account the nature and gravity of the breach in question and calculates an appropriate amount accordingly.
o This is the second time the CMA has issued Meta with a penalty for breaching its IEO. In October 2021, the firm was fined over £50 million after it significantly limited the scope of compliance reports, despite repeated warnings from the CMA. The reports were crucial to ensuring the CMA had oversight of the companies’ behaviour, including whether Meta had been taking any action which might prejudice the outcome of its investigation.
o The CMA issued its final decision in relation to the Meta and Giphy merger on 30 November 2021. This required Meta to sell Giphy in its entirety after finding the deal could harm social media users and UK advertisers.
§ The European Commission (EC) proposed “a comprehensive set of measures to ensure the EU's security of supply, resilience and technological leadership in semiconductor technologies and applications” per its statement. The EC stated:
o The European Chips Act will ensure that the EU has the necessary tools, skills and technological capabilities to become a leader in this field beyond research and technology in design, manufacturing and packaging of advanced chips, to secure its supply of semiconductors and to reduce its dependencies. The main components are:
o The Chips for Europe Initiative will pool resources from the Union, Member States and third countries associated with the existing Union programmes, as well as the private sector, through the enhanced “Chips Joint Undertaking” resulting from the strategic reorientation of the existing Key Digital Technologies Joint Undertaking. €11 billion will be made available to strengthen existing research, development and innovation, to ensure the deployment of advanced semi-conductor tools, pilot lines for prototyping, testing and experimentation of new devices for innovative real-life applications, to train staff and to develop an in-depth understanding of the semi-conductor ecosystem and value chain.
o A new framework to ensure security of supply by attracting investments and enhanced production capacities, much needed in order for innovation in advanced nodes, innovative and energy efficient chips to flourish. In addition, a Chips Fund will facilitate access to finance for start-ups to help them mature their innovations and attract investors. It will also include a dedicated semiconductor equity investment facility under InvestEU to support scale-ups and SMEs to ease their market expansion.
o A coordination mechanism between the Member States and the Commission for monitoring the supply of semiconductors, estimating demand and anticipating the shortages. It will monitor the semiconductor value chain by gathering key intelligence from companies to map primary weaknesses and bottlenecks. It will draw together common crisis assessment and coordinate actions to be taken from a new emergency toolbox. It will also react swiftly and decisively together by making full use of national and EU instruments.
o The Commission also proposes an accompanying Recommendation to Member States. It is a tool with immediate effect to enable the coordination mechanism between the Member States and the Commission to commence straight away. This will allow as from now to discuss and decide on timely and proportionate crisis response measures.
o The EC made available these documents:
§ European Chips Act: Questions & Answers
§ European Chips Act: Online Factpage
§ European Chips Act: Factsheet
§ The United Kingdom’s (UK) Information Commissioner’s Office signaled its ongoing interest in online advertising technology in a blog posting and stated:
o The Guardian’s TechScape newsletter gives an overview of recent discussions around cookies and online advertising, including Google’s plans to replace third party cookies with alternative technologies.
o We have been highly active in this space.
o In a Commissioner’s Opinion published last year, we set out clear data protection standards that companies must meet when developing online advertising technologies in order to safeguard people’s privacy. We have also intervened in other areas of the adtech industry.
o We are currently working with the Competition and Markets Authority to review Google’s plans from a competition and privacy perspective. You can read more about this work here.
§ The head of the White House’s Office of Science and Technology Policy (OSTP), a key entity in setting United States (U.S.) technology policy, is leaving the Biden Administration. OSTP Director Eric Lander resigned after Politico reported on his abusive behavior toward staff. Lander said in his resignation letter to President Joe Biden that he will serve only until 18 February to allow for an orderly transition at OSTP. One could deduce Lander was pushed out this week after he was not allowed to testify at a U.S. House Energy and Commerce Committee hearing nor to speak at an American Association for the Advancement of Science event.
§ The Netherlands’ Authority for Consumers and Markets (ACM) announced that “Apple has failed to satisfy the requirements set by the ACM regarding payment systems for dating-app providers. ACM has come to this conclusion following an investigation into Apple’s statements of January 15, 2022.” The ACM said “[t]his means that Apple now has to pay ACM the first penalty payment of 5 million euros.” The agency stated:
o Apple must adjust its conditions for access to the Dutch App Store for dating-app providers. In the App Store, dating-app providers must also be able to use payment systems other than Apple’s payment system. In addition, dating-app providers must have the ability to refer to payment systems outside of the app. This had been laid down in an order subject to periodic penalty payments that ACM imposed on Apple in August 2021. On December 24, 2021, the court ruled that this part of the order could be published.
o Apple has failed to satisfy the requirements on several points. The most important one is that Apple has failed to adjust its conditions, as a result of which dating-app providers are still unable to use other payment systems. At the moment, dating-app providers can merely express their ‘interest’. In addition, Apple has raised several barriers for dating-app providers to the use of third-party payment systems. That, too, is at odds with ACM’s requirements. For example, Apple seemingly forces app providers to make a choice: either refer to payment systems outside of the app or to an alternative payment system. That is not allowed. Providers must be able to choose both options.
o ACM has informed Apple that its statements do not satisfy the requirements laid down in the order subject to periodic penalty payments. Apple is still obligated to act in accordance with said order. If it fails to do so, Apple will have to pay each week a penalty payment of 5 million euros up to a maximum of 50 million euros.
§ The European Commission (EC) welcomed the “political agreement between the European Parliament and the Council on a stronger mandate for Europol, the EU agency for law enforcement cooperation.” The EC stated:
o Under this reinforced mandate, Europol will be able to step up its support to Member States in fighting serious crime and terrorism and tackling emerging security threats. Europol will be able to cooperate effectively with private parties. The updates also set clear rules on processing large and complex datasets, and allow the agency to develop new technologies that match law enforcement needs. These changes come with a reinforced data protection framework as well as stronger parliamentary oversight and accountability.
o The updated mandate includes:
§ Effective cooperation with private parties, in full compliance with strict data protection requirements. Terrorists often abuse the services provided by private companies to recruit volunteers, to carry out terrorist attacks and to disseminate their propaganda. Under its revised mandate, Europol will be able to receive personal data directly from private parties and analyse this data to identify those Member States that could open investigations into related crimes. Such cooperation will remain subject to strict data protection requirements.
§ Clear rules on the analysis of “big data” by Europol to support criminal investigations, in compliance with fundamental rights. The processing of large data sets is an integral part of today's police work, and Europol's role is essential in detecting criminal activities that escape the analysis by individual Member States. The new mandate provides legal clarity on the pre-analysis of big data by Europol, addressing also recent decisions by the European Data Protection Supervisor. Europol will have 18 months to pre-analyse big data received from Member States and give it a data subject categorisation, with a possible extension for another 18-month period.
§ A support role for Europol in issuing information alerts on foreign terrorist fighters. Europol will be able to propose that Member States enter in the Schengen Information System information received from non-EU countries on suspects and criminals, in particular foreign fighters. This will make such information directly available to officers at the Union's external borders and within the Schengen area.
§ Reinforced cooperation with non-EU countries as serious crime and terrorism often have links beyond the territory of the Union.
§ Improved cooperation with the European Public Prosecutor's Office. Through a hit/no-hit system, the European Public Prosecutor's Office will be able to have indirect access to Europol data in relation to offences within its mandate, in line with the applicable safeguards. This will support criminal investigations and prosecutions.
§ A new role for Europol in research and innovation to identify new technology needs for law enforcement, helping to equip national law enforcement authorities with modern IT tools to counter serious crime and terrorism.
§ Further strengthened data protection framework at Europol to make sure Europol continues to have one of the most robust data protection frameworks in the world of law enforcement, in line with EU rules on data protection.
§ Reinforced supervision of Europol, with additional powers for the European Data Protection Supervisor and a new Fundamental Rights Officer at Europol.
§ Strengthened parliamentary oversight and accountability, with a reinforced role for the Joint Parliamentary Scrutiny Group (in charge of monitoring the agency's activities), advised by a Consultative Forum.
§ The United Kingdom’s (UK) Information Commissioner’s Office (ICO) is inviting organisations in the health sector to participate in workshops on privacy-enhancing technologies (PETs). The ICO added:
o We want to set out how PETs can facilitate safe, legal and valuable data sharing in health and understand what’s needed to help organisations use these technologies. The information gathered from the workshops will help the ICO develop updated guidance and advice.
o Privacy-enhancing technologies refer to a broad range of processes and approaches for protecting personal data. PETs help organisations to implement and improve data protection by design. This could be through traditional methods such as encryption, or more advanced solutions.
o But adoption of PETs is low.
§ American, Australian, and British security agencies have issued their first joint ransomware advisory that “provides observed behaviors and trends as well as mitigation recommendations to help network defenders reduce their risk of compromise by ransomware.” The United States (U.S.) Federal Bureau of Investigation (FBI), the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the U.S. National Security Agency (NSA), the Australian Cyber Security Centre (ACSC), and the United Kingdom (National Cyber Security Centre (NCSC) noted:
o In 2021, cyber authorities observed a number of ransomware trends, including:
§ increased use of cyber criminal ‘services-for-hire’;
§ sharing of victim information between different groups of cyber criminals, and;
§ diversifying approaches to extorting money.
o Ransomware groups also increased the impact of their attacks by:
§ targeting cloud services;
§ attacking industrial processes and the software supply chain, and;
§ launching attacks on organisations during public holidays and weekends.
o …that if the ransomware criminal business model continues to yield financial returns for ransomware actors, ransomware incidents will become more frequent. Every time a ransom is paid, it confirms the viability and financial attractiveness of the ransomware criminal business model. Additionally, cybersecurity authorities in the United States, Australia, and the United Kingdom note that the criminal business model often complicates attribution because there are complex networks of developers, affiliates, and freelancers; it is often difficult to identify conclusively the actors behind a ransomware incident.
o The FBI, CISA, and NSA observed incidents involving ransomware against 14 of the 16 U.S. critical infrastructure sectors, including the Defense Industrial Base, Emergency Services, Food and Agriculture, Government Facilities, and Information Technology Sectors.
o The ACSC observed continued ransomware targeting of Australian critical infrastructure entities, including in the Healthcare and Medical, Financial Services and Markets, Higher Education and Research, and Energy Sectors.
o The NCSC-UK recognizes ransomware as the biggest cyber threat facing the United Kingdom. Education is one of the top UK sectors targeted by ransomware actors, but the NCSC-UK has also seen attacks targeting businesses, charities, the legal profession, and public services in the Local Government and Health Sectors.
§ Meta/Facebook’s Oversight Board published its first advisory opinion “on the sharing of private residential information” and associated risks of doxing. The Board summarized its findings, recommendations, and the background:
o In its policy advisory opinion, the Board recommends that Meta remove the exception to the Privacy Violations Community Standard that allows the sharing of private residential information when it is considered “publicly available.” This would help Meta better protect people’s private residential information.
o Among its other recommendations, the Board proposes that Meta create a communications channel for victims of doxing, give users more control over how they consent to sharing their private residential information and provide data showing the amount of content removed following privacy-related government requests.
o Last year, Meta requested a policy advisory opinion from the Board on the sharing of private residential addresses and images, and the contexts in which this information may be published on Facebook and Instagram. Meta considers this to be a difficult question as while access to such information can be relevant to journalism and civic activism, “exposing this information without consent can create a risk to residents’ safety and infringe on an individual’s privacy.”
o Meta’s request noted several potential harms linked to releasing personal information, including residential addresses and images. These include “doxing,” (which refers to the release of documents, abbreviated as “dox”) where information which can identify someone is revealed online. Meta noted that doxing can have negative real-world consequences, such as harassment or stalking.
§ A Swedish tech firm is suing Alphabet/Google after the European Commission’s €2.42 billion antitrust fine was upheld in a ruling by the General Court of the European Union (EU). As the court explained “By decision of 27 June 2017, the Commission found that Google had abused its dominant position on the market for online general search services in 13 countries in the European Economic Area, by favouring its own comparison shopping service, a specialised search service, over competing comparison shopping services.” Google may exercise the last appeal available by having the Court of Justice for the European Union hear the case. PriceRunner, “the UK’s largest comparison service with 2.3 million products from 6,000 retailers in 21 different countries, who all deliver to the UK,” claimed in its press statement:
o PriceRunner has today sued Google for a preliminary amount of almost EUR 2.1 billion (SEK 22 billion) at the Patent and Market Court in Stockholm. The lawsuit follows the conclusion of the European General Court which established that Google has breached EU antitrust laws by manipulating search results in favour of their own comparison shopping services. Google has thereby caused harm to European consumers who overpay when shopping online as well as to PriceRunner and other comparison shopping services. Since the violation is still ongoing the amount of damages increases every day, we expect the final damages amount of the lawsuit to be significantly higher.
§ The Federal Communications Commission (FCC) “announced that it is committing $125,962,023.72 in its ninth wave of Emergency Connectivity Fund program support…[that] will support over 270,000 students and provide funding for 340 schools, 20 libraries and 6 consortia, which are approved to receive over 330,000 connected devices and over 39,000 broadband connections.” The FCC stated:
o Since its June 2021 launch, the program has committed over $4.5 billion supporting all 50 states, Guam, Puerto Rico, the U.S. Virgin Islands, the Northern Mariana Islands, and the District of Columbia.
o The funding can be used to support off-campus learning, such as nightly homework, to ensure students across the country have the necessary support to keep up with their education. Total commitments to date are supporting over 10,800 schools, 875 libraries, and 125 consortia for nearly 9.9 million connected devices and over 4.9 million broadband connections. Today’s announcement includes nearly $27 million in commitments from Window 1 applications and over $99 million in commitments from Window 2 applications.
§ An organization formed by Twitter has announced the formation of a public benefit limited liability corporation “to develop and drive large-scale adoption of technologies for open and decentralized public conversation.” Bluesky explained that “Bluesky PBLLC, a Public Benefit LLC that will implement that vision as an independent organization.” The organization stated:
o We envision an open social media ecosystem where developers have more opportunity to build and innovate, and users have more choice and control over which services they use and their experience on social media as a whole. The development and adoption of decentralized protocols is a path we see towards establishing a strong technical foundation for permissionless innovation and user choice. Decentralization is a structural change that in itself is insufficient for creating a healthy social media ecosystem. However, by creating an environment where developers can freely build, communities can self-govern, and users can easily switch services, decentralization can catalyze the innovation necessary to improve the public conversation.
o The many existing decentralized social networks that currently make up the ecosystem can be categorized into federated and p2p architectures. Our approach will be to combine the best of both worlds by integrating the portability of self-certifying protocols with the user-friendliness of delegated hosting, so users don’t have to run their own infrastructure and developers can build performant apps. Moderation is an important part of any online social forum, which is why we will proactively build tooling for reputation and moderation systems that are transparent, opt-in, and multi-layered, as well as create frameworks for others to build such tooling. We’re building on existing protocols and technologies but are not committed to any stack in its entirety. We see use cases for blockchains, but Bluesky is not a blockchain, and we believe the adoption of social web protocols should be independent of any blockchain.
o Our current focus is on building and releasing a prototype that illustrates our approach. Stay tuned for news about our new team members soon. To participate in the community and follow our progress, join the bluesky community, or follow our Twitter account for updates.
Further Reading
Photo by Tetyana Kovyrina from Pexels
§ “The hacked account and suspicious donations behind the Canadian trucker protests” By Anya van Wagtendonk, Benjamin Powers, and Steve Reilly — Grid News. Hundreds of people have been camped out in the icy streets of Ottawa, Canada’s capital city, for more than a week, occupying the area around the nation’s government buildings. It’s a protest ostensibly stemming from some Canadian cross-border truckers’ objections to a Canadian requirement that those who cross the border be vaccinated against covid-19. But a close look at several “Freedom Convoy” groups and crowdfunding efforts online shows the involvement of anonymous actors, deep-pocketed non-Canadian donors and prominent U.S. right-wing political figures.
§ “The DOJ’s $3.6B Bitcoin Seizure Shows How Hard It Is to Launder Crypto” By Andy Greenberg — WIRED. On Tuesday, Ilya Lichtenstein and Heather Morgan were arrested in New York and accused of laundering a record $4.5 billion worth of stolen cryptocurrency. In the 24 hours since, the cybersecurity world has ruthlessly mocked their operational security screwups: Lichtenstein allegedly stored many of the private keys controlling those funds in a cloud-storage wallet that made them easy to seize, and Morgan flaunted her “self-made” wealth in a series of cringe-inducing rap videos on YouTube and Forbes columns.
§ “Meet the NSA spies shaping the future” By Patrick Howell O’Neal — MIT Technology Review. For someone with a deeply scientific job, Gil Herrera has a nearly mystical mandate: Look into the future and then shape it, at the level of strange quantum physics and inextricable math theorems, to the advantage of the United States.
§ “The age of intimacy famine: when we interact with our phones rather than our loved ones” By Michelle Drouin — The Guardian. Like most humans, I want intimacy. But as a developmental psychologist, I consider intimacy a fundamental human need. Sharing feelings, embraces, intellectual conversations, sex – these intimate moments are often the touchstones of a rich human experience. Yet millions of people worldwide are isolated and lonely, woefully lacking in the meaningful and diverse social experiences that help support emotional and physical health.
§ “CFTC Chair Asks Congress for Authority to Regulate Some Cryptocurrencies” By Paul Kiernan — The Wall Street Journal. “The head of the Commodity Futures Trading Commission called on lawmakers Wednesday to grant his agency authority to regulate cryptocurrencies such as bitcoin, saying the “speculative fervor” around such assets has left investors in need of protection.
§ “The metaverse is a new word for an old idea” By Genevieve Bell — MIT Technology Review. I have spent a lot of my career, both in Silicon Valley and beyond, insisting that all our technologies have histories and even pre-histories, and that far from being neat and tidy, those stories are in fact messy, contested, and conflicted, with competing narrators and meanings.
§ “How Telegram Became the Anti-Facebook” By Darren Loucaides — WIRED. On January 6, 2021, as a crowd of Donald Trump supporters began gathering for a rally near the foot of the Washington Monument, Elies Campo was spending a poignant afternoon at his family's home in Tortosa, Spain. January 6—the feast of the Epiphany, or Three Kings Day—is the high point of the holiday season there, when relatives visit and children open their presents. And Campo, a 38-year-old Spanish engineer who lives in Silicon Valley, had been largely stranded away from home since the start of the coronavirus pandemic. As he moved through the house, Campo was surrounded by uncles and aunts and cousins, and he got to hold a couple of their babies for the first time. His mind was about as far from the United States as it could possibly be.
§ “Local Papers Find Hints of Success With Online Subscriptions” By Marc Tracy — The New York Times. When the hedge fund Alden Global Capital bid to buy the newspaper chain Lee Enterprises in November, many journalists at Lee’s newspapers opposed a sale because Alden had slashed newsroom costs at the newspapers it owns.
§ “Twitter Tells U.S. Senator It’s Cutting Ties to Swiss Tech Firm” By Ryan Gallagher — Bloomberg. Twitter Inc. told a U.S. senator it is cutting ties with a European technology company that helped it send sensitive passcodes to its users via text message. The social media firm said in a disclosure to U.S. Senator Ron Wyden, a Democrat from Oregon, that it is “transitioning” its service away from working with Mitto AG, according to a Wyden aide.
§ “Europe has a chips plan — here are 6 things that could kill it” By Laurens Cerulus and Joshua Posaner — Politico EU. The EU on Tuesday presented a €43 billion plan to turbo-charge its microchips sector by 2030. For it to work it'll have to overcome a terrible track record on industrial policy. The Commission's new European Chips Act is an attempt to shore up the bloc's capacity to produce semiconductors, tiny pieces of technology that are critical to everything from cars to smartphones. The plan aims to "make Europe a leader in this market,” Commission President Ursula von der Leyen said Tuesday. "Chips are crucial in almost every device. But the pandemic has also painfully exposed the vulnerability of chips supply chains."
§ “Kids are flocking to Facebook’s ‘metaverse.’ Experts worry predators will follow.” By Will Oremus — The Washington Post. I was alone in the virtual world, meandering through a side corridor of a simplistically rendered palace, when a stranger entered. “Hello?” a small voice called from the palace’s central plaza. “Where are you?” I hesitated. The voice sounded like it belonged to a child. “I can’t find you,” the child said, plaintively. “Can you give me a hint?” In theory, kids aren’t allowed in the game. The new virtual-reality app Horizon Worlds, the first foray into the much-hyped “metaverse” for Facebook parent company Meta, is limited to adults 18 and older.
§ “The Spanish-language misinformation crisis” By Ashley Gold and Russell Contreras — Axios. Spanish-language misinformation on social media platforms is flourishing, even as tech companies add more moderators, adopt stricter content rules, add context labels and block offending accounts.
§ “Why the balance of power in tech is shifting toward workers” By Jane Lytvynenko — MIT Technology Review. If executives at Facebook and other tech companies hoped Haugen would be an outlier, Ifeoma Ozoma had other plans: a day after Haugen’s testimony, Ozoma and several colleagues launched the Tech Worker Handbook online. Ozoma was herself a whistleblower, having called out racial and gender discrimination at Pinterest, together with her coworker Aerica Shimizu Banks, in 2020. Since then, she has become something of an inspiration for whistleblowers in the tech world. “I’ve heard from tech workers asking for advice since I first went public,” she says. She responded to hundreds of people individually, but to her that solution was just “not scalable,” so she used what she’d learned from those experiences to build the website. It got 30,000 hits on the first day.
§ “Amazon Labeled a Grocer by U.K Watchdog, Must Abide by New Rules” By Katie Linsell and Dierdre Hipwell — Bloomberg. Britain’s antitrust regulator designated Amazon.com Inc. as a grocery retailer, subjecting the online retail giant to the same rules followed by U.K. supermarket chains, such as Tesco Plc.
Coming Events
Photo by Canva Studio from Pexels
§ 10 February
o The United States Judiciary Committee will consider the following bills and nominations:
§ The EARN IT Act of 2022 (S.3538)
§ 17 February
o The U.S.-China Economic and Security Review Commission will hold a hearing titled “China’s Cyber Capabilities: Warfare, Espionage, and Implications for the United States.”
§ 18 February
o The Federal Communications Commission (FCC) will hold an open meeting with this agenda:
§ Promoting Telehealth in Rural America. The Commission will consider a Further Notice of Proposed Rulemaking that would seek comment on reforms to the urban and rural rates determination process for the Rural Health Care Program’s Telecommunications Program, revisions to Rural Health Care Program rules governing the internal funding cap on upfront payments and multi-year contracts, and modifications to the Rural Health Care Program invoicing procedures. (WC Docket No. 17-310)
§ Aureon Refund Data Order. The Commission will consider an Order requiring Iowa Network Access Division (d/b/a Aureon) to file cost and demand data to enable Commission staff to calculate appropriate refunds due to Aureon’s customers after two investigations into Aureon’s tariffed switched transport rate. (WC Docket No. 18-60)
§ Updating Technical Rules for Radio Broadcasters. The Commission will consider a Report and Order to eliminate or amend outmoded or unnecessary broadcast technical rules. (MB Docket No. 21-263)
§ Enforcement Bureau Action. The Commission will consider an enforcement action
§ 22 February
o The European Data Protection Board (EDPB) will hold a plenary meeting.
§ 16-17 June
o The European Data Protection Supervisor will hold a conference titled “The future of data protection: effective enforcement in the digital world.”